Is Your Web Application Secure?
Our security engineer will test and detect the vulnerabilities luring in your web applications.
As the relationship between information assets and the internet deepens, cybercriminals on web application vulnerabilities are increasing in recent years.
If you leave the vulnerabilities unpatched:
- The critical and personal information stored in database may leak outside
- Your service may be maliciously manipulated
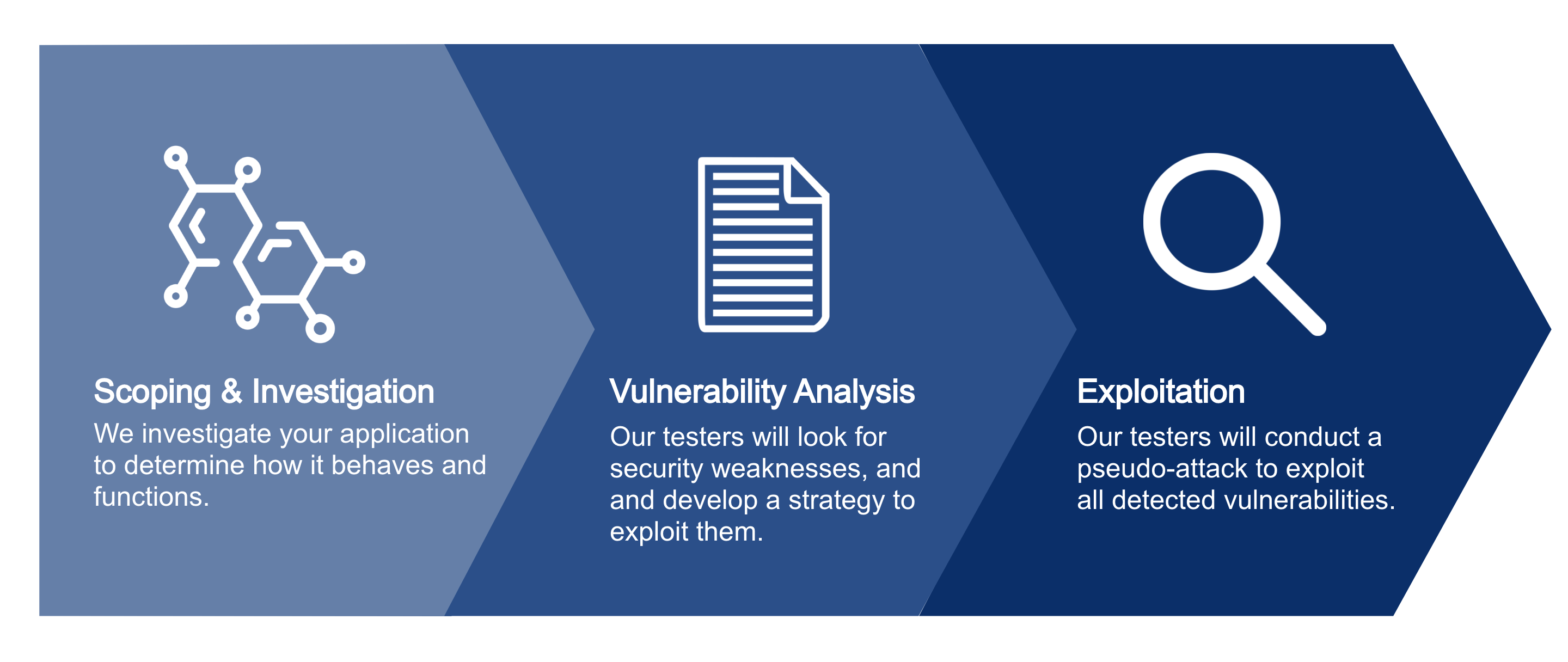
What is Web Application Vulnerability?
Web application vulnerability is the internal bug of a program within the application, which makes your information exposed to exploitation.
Because web applications are designed according to your needs with multiple functions, the locations of vulnerability could be anywhere; there are various programming languages, and web application types are also diverse. Examples of web application types are EC site, a game application, SNS, and Back Office. You may also need to take into account whether you have CMS installed or not.
Details
Ways of web application development differ depending on the companies and the persons in charge, which means that the vulnerabilities also vary. Because of this, you will likely overlook vulnerabilities with assessment tools on the market.
It is necessary to comprehend the structure and characteristics of each web application and run thorough assessments.
To secure your system, our experienced security engineers provide vulnerability assessments to prevent system halt, falsification, unauthorized access, SQL injection attacks, cross-site scripting.
Leaving your vulnerabilities does not only make you a victim of damages such as information leakage but also be manipulated to attack other websites, making you a perpetrator.
Description
- We diagnose whether if you are taking appropriate security protection measures on personal information and confidential information.
- We look for internal security issues: We run diagnosis on XSS, SQL Injection, CSRF, Open Redirect, Command Injection, deficiency in authentication function, Application Logic, etc. via network.
At the briefing conference, our security engineers will give you a detailed report and recommended solutions for the issues detected.
Correspondence to security standards such as PCI DSS, CIS, NIST, etc.
The service targets vulnerability such as OWASP Top 10* listed in PCI DSS, the security standards of the credit card industry.
*OWASP is an American organization aiming for improvement in web application security. They have their deliverables from investigation and development available to the public.
*Top 10 web application vulnerabilities are listed in the OWASP Top Ten Project.
Types of Assessments:
- Tool based
- Tool and manual
Assessment location:
- On-site
- Remote
By taking measures according to the assessment results, you can prevent damages such
as SQL injection, cross-site scripting, session hijacking.
There are generally three ways to run the assessment: 1) Tool based (automatic), 2) manual diagnostics, 3) Both 1) and 2).
Although the diagnostic tools are the most efficient, there is a risk of overlooking and false detections. At Belue Creative, we encourage our clients to run a thorough assessment
using both automated and manual methods.
Web Application Assessment Subjects
The following are examples. Please feel free to contact us for more information.
- A members-only website
- E-commerce
- Survey site
- Reservation system
- Online banking
- Internet trading
- Various information providers with searching engines
- Business management site for internal use
- Websites for smartphones and mobile phones.
- Blog
- e-Learning
- Web API
We still recommend running assessments by experienced professionals for companies that have already run diagnostics with commercial software or home assessments.
What you get:
- a. Optimization of the cost and duration of security measures through a precise diagnosis by security engineers
- b. Risk mitigation of personal information leakage, and damages contingent to compensatory damages, etc.
- c. Objective assessment report that can be used as a report for external inspection
What you’ll find if attackers can:
- Steal identity and illegally access the system?
- Obtain important information such as personal information and confidential information?
- Gain administrative right?
- Access the database?
- Access to restricted resources?
Major Scanning Items
- Cross-Site Scripting test
- SQL Injection risk assessment
- Second order attack
- Forced browsing
- Error code
- Cookies without secure attribute set
- Session management security issues
- Insufficient access control mechanism
- Abuse of database functions
- Denial of Service (DoS) attack
- Insufficient authentication
- Application logic vulnerability
Additional options
- IPv6
- DoS attack
- Brute force (tolerance of authentication)
Our Approach